From Youtube Ads to Android Banking Trojans
A good way to find out malware is to look through the ads, normally there are youtube ads with gambling applications but this time I found a backdoor. This is the first time I actually got a TP backdoor in ads.
The usual signal of this application was that it was a PDF reader and had 1K installations.
AndroidManifest had the permission REQUEST_INSTALL_PACKAGES, which is a signal that the application can install other applications. Used commonly by droppers. The next step was to find where the application was using this permission, so I used jadx-gui to decompile the application and search for the permission. I searched for package/vnd.android.package-archive but I couldn’t find anything, so I searched for “https://” and found the following code:
Two C2’s were hardcoded in the application in plain text with the same domain, they contained binaries that were downloaded and executed in the device. I won’t go into detail how the payload was downloaded and executed, I found this while I was reversing another application and I wanted to provide a quick write-up about it. All C2’s were saved in wayback machine.
https://dulinare[.]com/pdffilehttps://dulinare[.]com/hanihani(malicious dex file)
Loading the dex file there were only 4 classes, I searched around them and could see an anti-emulator check and geo-location check. Seems to be targeting the following ISO’s:
- es, sk, si, sl, bg, gb, cn, fi, hu, ie, pt
Another C2 was found, this one had the actual backdoor:
https://sefuban[.]com/1.apk
Installing this last APK, quickly asked for accessibility permissions and started to send the following information to the C2:
http://185.215.113[.]31:85/api/getkeyloggershttp://185.215.113[.]31:85/api/botupdatehttp://91.215.85[.]55:85/api
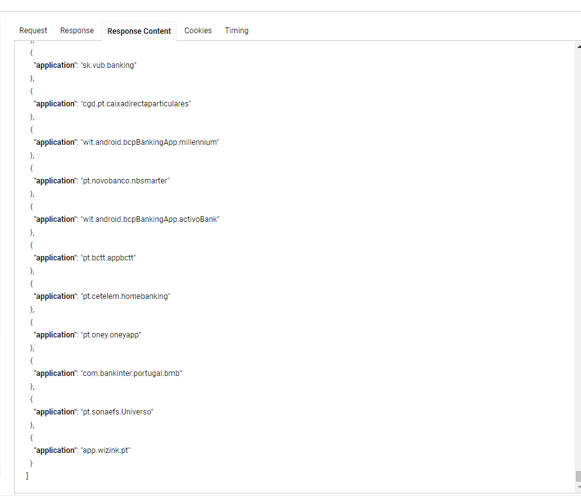
I haven’t looked much into what the backdoor actually did, but the url /api/getkeyloggers is a good signal that it was a keylogger. Inside the C2, there were multiple banks and applications, so it was probably a banking trojan targeting also Portuguese people.
For example, the following banks were targeted and much more:
- com.binance.dev
- pt.santander.oneappparticulares
- com.revolut.business
- com.santandermovelempresarial.app
- de.traderepublic.app
- ie.avantmoney.mobileapp
- com.comtrade.simba.gbkr
- dbs.mobileBankingProd
- com.hrc.eb.mobile.android.hibismobilelon
- com.hrc.eb.mobile.android.hibismobilevipava
- bg.ccbmobile.app
- bg.allianz.banking
- com.openintegra.dsk_smart_business
- sk.vub.banking
- cgd.pt.caixadirectaparticulares
- wit.android.bcpBankingApp.millennium
- pt.novobanco.nbsmarter
- wit.android.bcpBankingApp.activoBank
- pt.bctt.appbctt
- pt.cetelem.homebanking
- pt.oney.oneyapp
- com.bankinter.portugal.bmb
- pt.sonaefs.Universo
- app.wizink.pt
Encryption/decryption algorithm of the requests is XOR with the key 66 decimal.
SHA256 DIGESTS of the samples:
- 95765ba9ade111c579d53d10585f594af6241f32599d084b4646316facc491aa
- 6b49ff162980515a62a716c76b0c170f80dd01e5b533c2a458ddf88bc74eb49d